Live Demos from the Forescout European Engineering Team.
Join us weekly for live 20 mins demos
Register for Live Demo
Details
Time:
- 12:30-12:50 BST / GTM (20 mins)
- 13:30-13:50 CEST/ CET (20 mins)
- 15:30-15:50 EEST/ EET (20 mins)
Dates:
- Fri 18 Aug (Network Security)
- Fri 25 Aug (REM)
- Fri 1 Sept (TD&R)
- Fri 8 Sept (OT security)
- Fri 15 Sept (Network Security)
- Fri 22 Sept (REM)
- Fri 29 Sept (TD&R)
- Fri 6 Oct (OT security)
- Fri 13 Oct (Network Security)
- Fri 20 Oct (REM)
- Fri 27 Oct TD&R)
- Fri 3 Nov (OT security)
- Fri 10 Nov (Network Security)
- Fri 17 Nov (REM)
- Fri 24 Nov (TD&R)
- Fri 1 Dec (OT security)
- Fri 8 Dec (Network Security)
Where:
Virtual
Hosts:
European Engineering Team
Contact Us:
Chris Hepple
European Marketing
[email protected]
Virtual
Hosts:
European Engineering Team
Contact Us:
Chris Hepple
European Marketing
[email protected]
Demo Overview
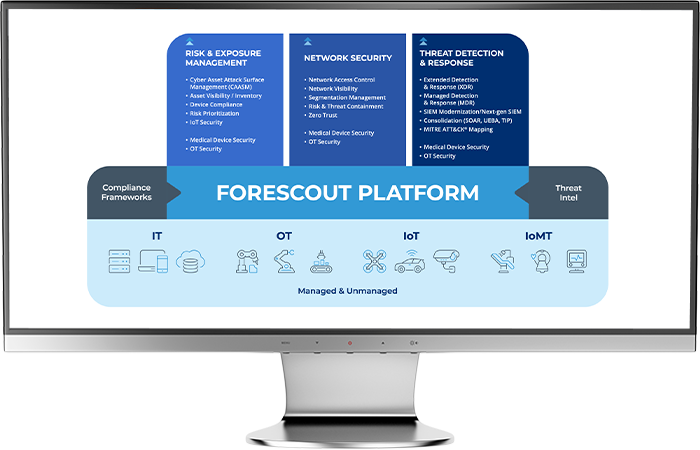
Network Security
Discover, assess and enforce the compliance of all connected assets to ensure network security.
Demo highlights:
- Hybrid platform for modern on-premise / cloud environments.
- Continuously discover and classify all physical and virtual devices connected to your network without agents and scans.
- Assess the security posture of all connected devices and priorities fixes.
- Report real-time hardware and software asset inventory audits.
- Continuously assess if networked devices are running up-to-date security software.
- Limit access to employees when they are of out of compliance.
- Set policies to automate the controls of vulnerable hosts, unpatched assets or infected systems.
- Assess devices and restrict, block or quarantine noncompliant systems.
- Segment access based on device type and security posture to reduce the risks posed by rogue devices or noncompliance.
Risk and Exposure Management
Enhance your network security posture with risk-based prioritization.
Demo highlights:
- Cloud platform with modern asset view.
- Maintain a persistent asset inventory that tracks device-status-over-time.
- Quantification of risk from configuration, function, and behavior.
- Using risk and exposure attributes to design security policies and remediation workflows.
- How to leverage risk-based prioritization for incident response.
Threat Detection & Response
Improve Your SOC Efficiency by 450x with better Detection and Response of true threats
Demo highlights:
- Intuitive UI designed for SOC analysts
- MITRE ATT® integration
- Easy to add data sources
- Automated data enrichment (IP geolocation, user and asset information).
- Two-stage threat detection engine applies a blend of five detection techniques
- Tiered storage (Hot, Warm, Cold) with rapid full-text search
- Comprehensive detection rules with intuitive custom rules creation
- Pre-configured, customizable, persona-based dashboards
- Case management integration with 3rd party solutions
- Integration with other Forescout solutions
OT Security
Reduce operational and security risk in OT/ICS and SCADA environments
Demo highlights:
- Passive monitoring and DPI of 250+ OT, IoT and IT protocols for in-depth monitoring and non-intrusive OT/ICS vulnerability identification.
- Active endpoint discovery specific to OT/ICS inventory, audit, and compliance requirements.
- Integration with network infrastructure to identify assets the moment they connect to the network.
- Automated OT asset information and configuration change logs for security analysis and compliance reporting.
- Real-time detection and controls providing guardrails for misconfigurations or operational errors.
- Intuitive compliance reporting for key standards NERC CIP, EU NIS Directive, NIST CSF and IEC 62443.
- NAC applied to contractor or remote employees, checking their security posture before granting access to the network and critical assets.
- Information-sharing across IT and security products, including ITSMs, SIEMs, firewalls, authentication servers, for better situational awareness.



